

ARKEN
One Platform, All Controls!
ARKEN is a hardware/software solution that bridges the gap between Information Security Controls and Information Technology Administration. Our platform gives you the ability to apply Information Security Policy, Standards, and Controls throughout the Information Technology Infrastructure and User base.
A cybersecurity incident, an attack, most often causes panic at all levels within an organization. It is at this point that the realization is made that endpoint and edge security simply do not provide the ability to quickly mitigate the incident nor provide the best recovery options.
ARKEN delivers a set of tools, both manual and automated, in one user-friendly interface. Typical information security management requires a set of different software/hardware tools and most often multiple resources at great expense to the organization. ARKEN alleviates that burden. ARKEN’s interface provides the functionality for system administrators, information security engineers, analysts, and auditors to coordinate cybersecurity activities more accurately across networks and attached devices, without placing an undue burden of information technology staff.
Arken Features
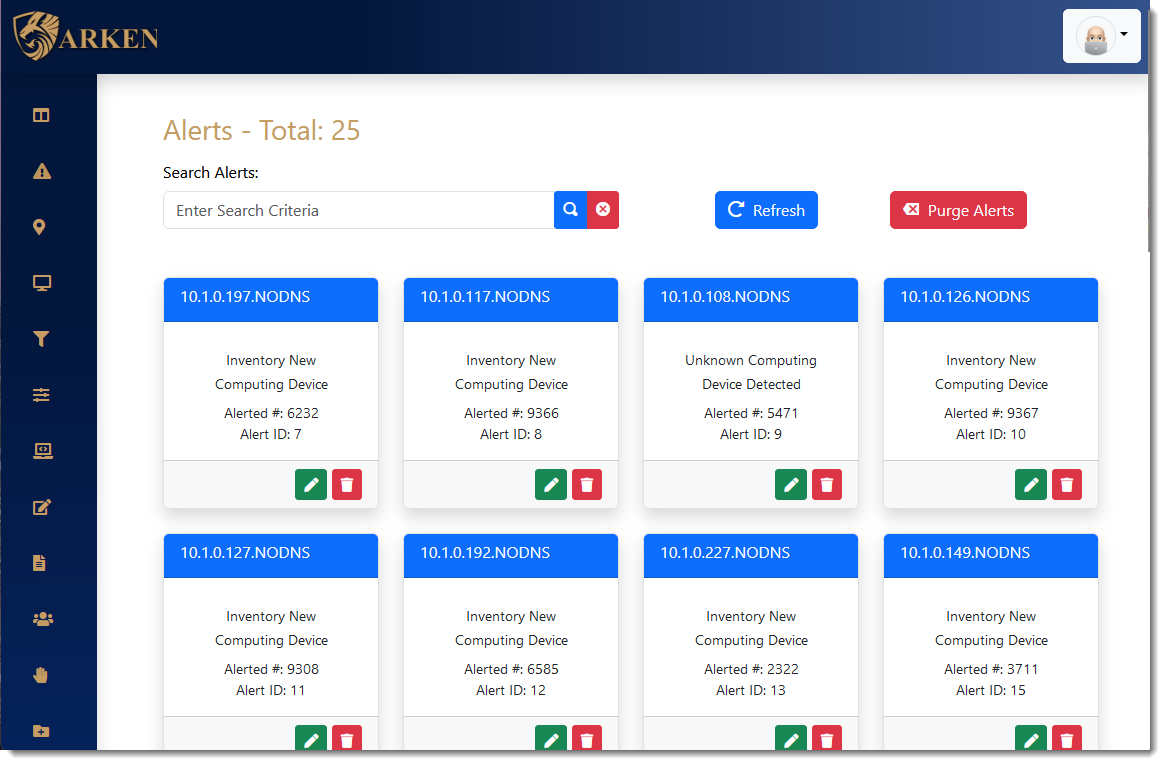
Alerts
The Alerts dashboard in ARKEN provides a real-time, incident response-oriented approach to quick resolution of issues. Alerts are generated from defined Incident Response Procedures and can contain both automated and manual activities.
As alerts are worked, all aspects of the alert resolution are audited and reported.
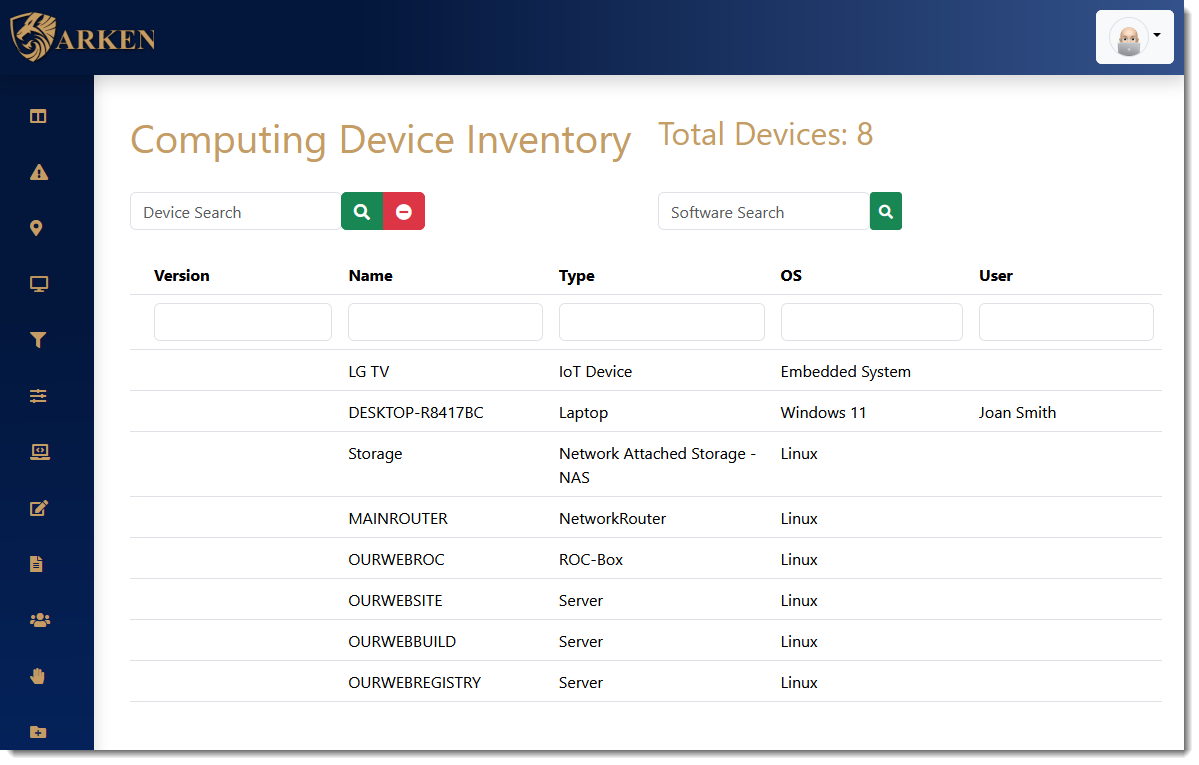
Positive Inventory
Install ARKEN and it will discover all operational devices automatically. ARKEN furnishes identification scans and integrates with Active Directory and/or LDAP.
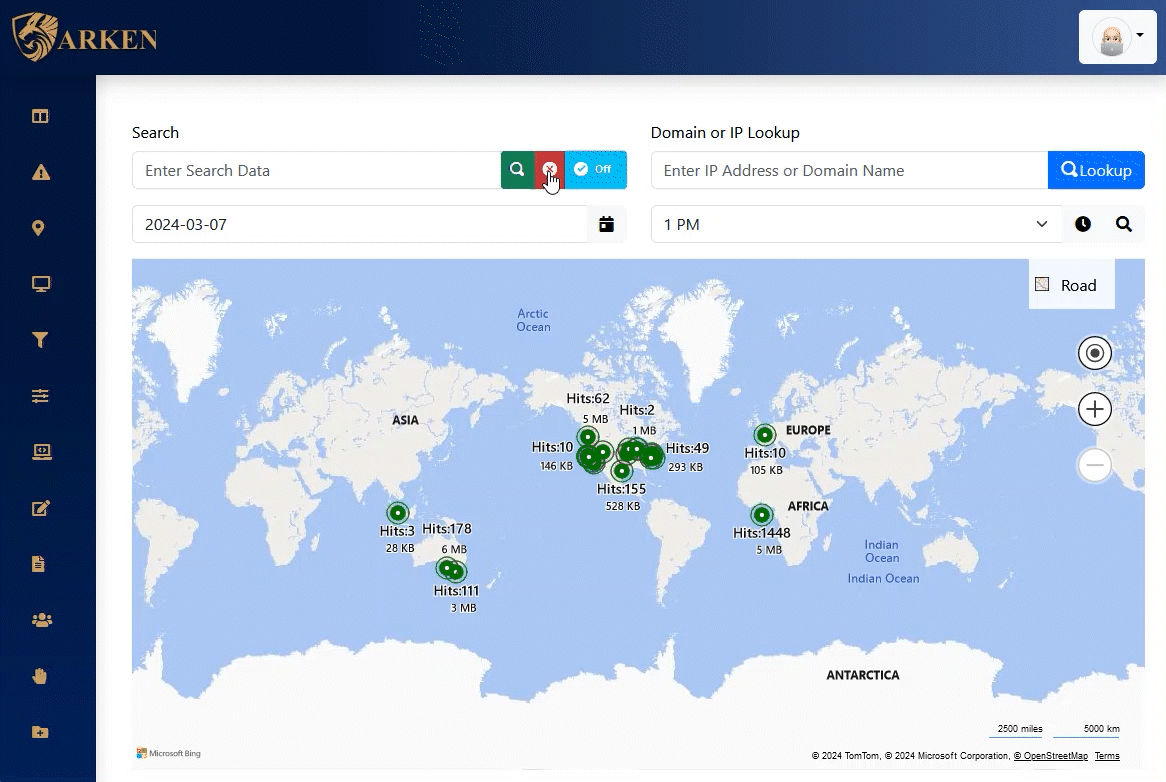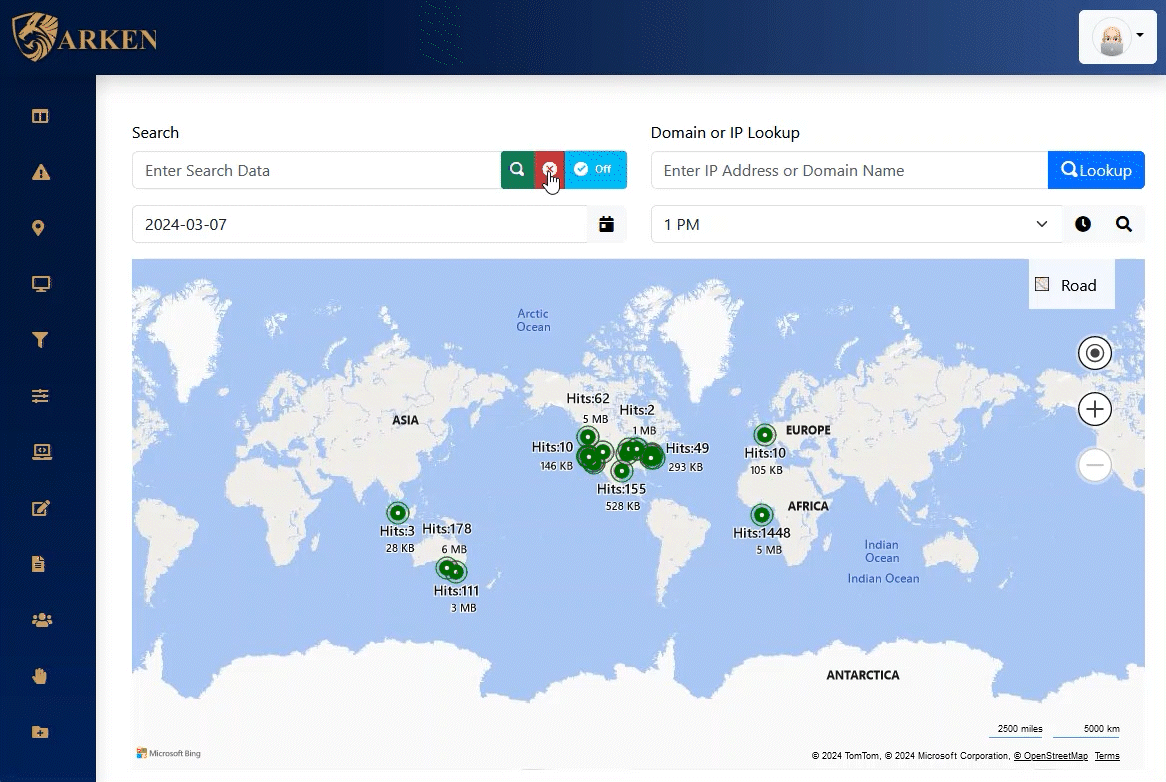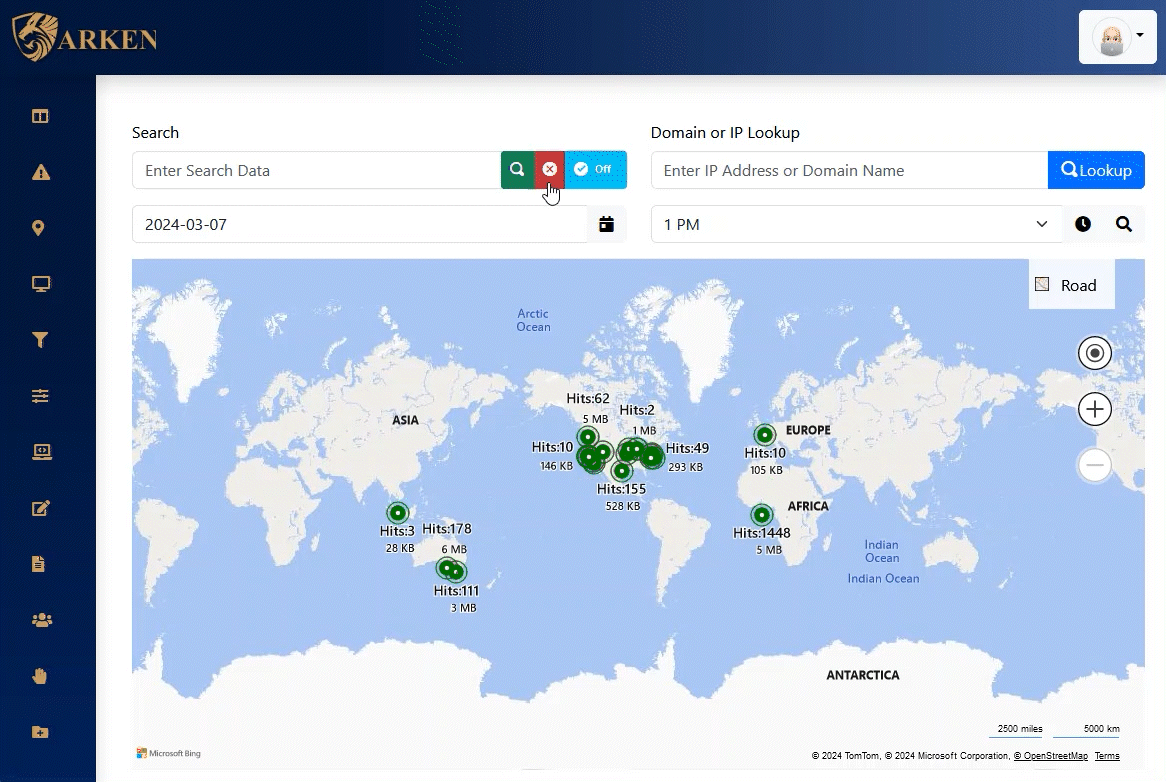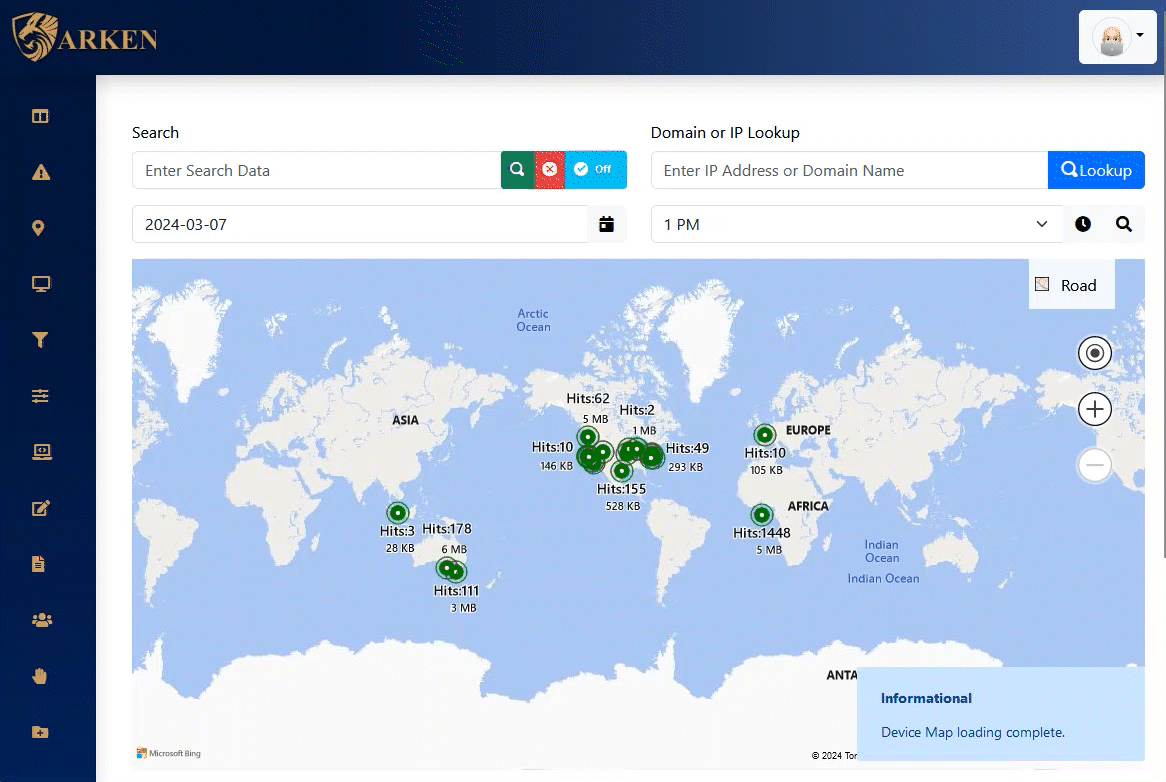
Network Traffic Mapping
Get a “visual view” of all external computing devices that are being accessed from within your environment. Identify Domain, Organization, ISP, State/Province, and Country that your internal devices are accessing. Control access with immediate filtering and restriction as required.
Network Traffic Filtering
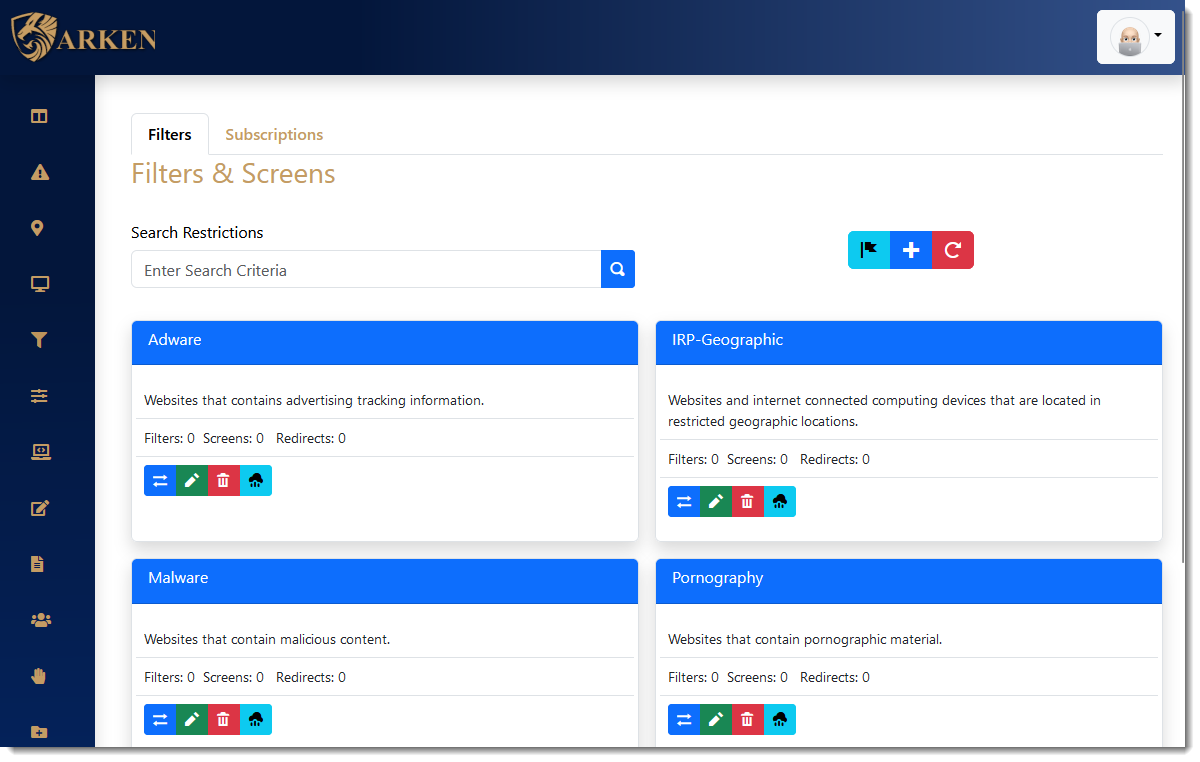
Apply IP address restriction and DNS filtering at the edge and/or within each Class C network subnet. Apply different filtering and restriction based on User, Group, or Device purpose.
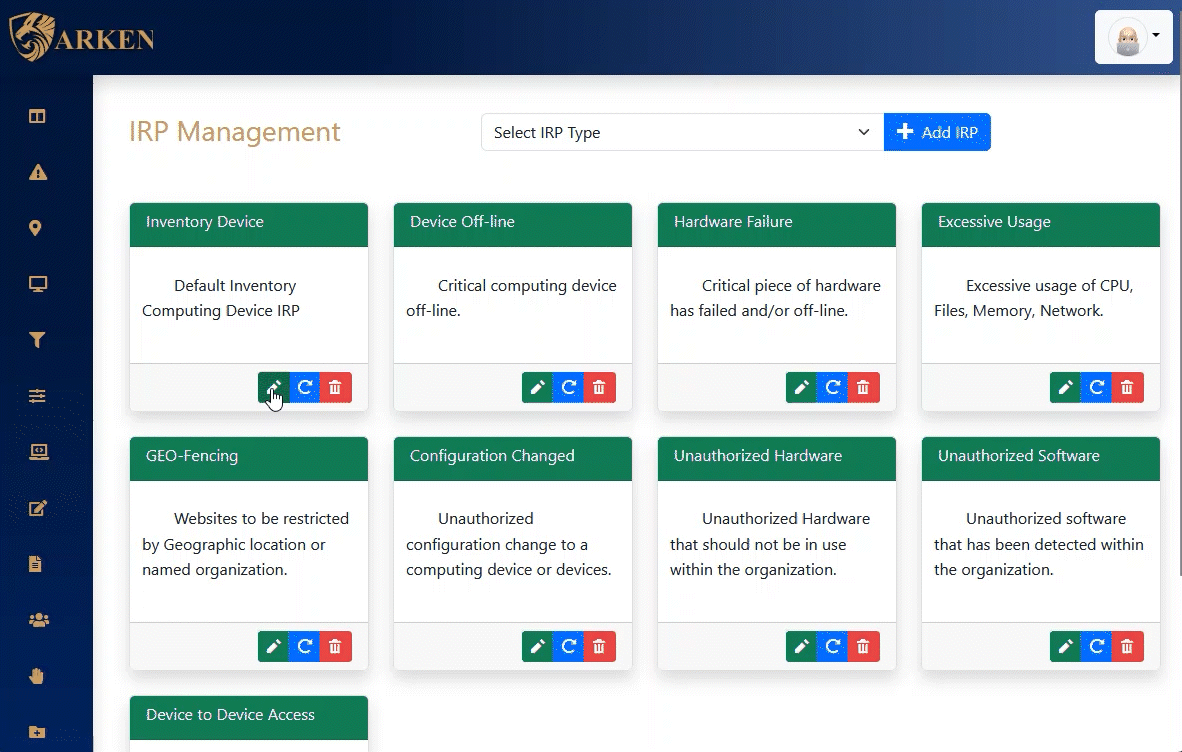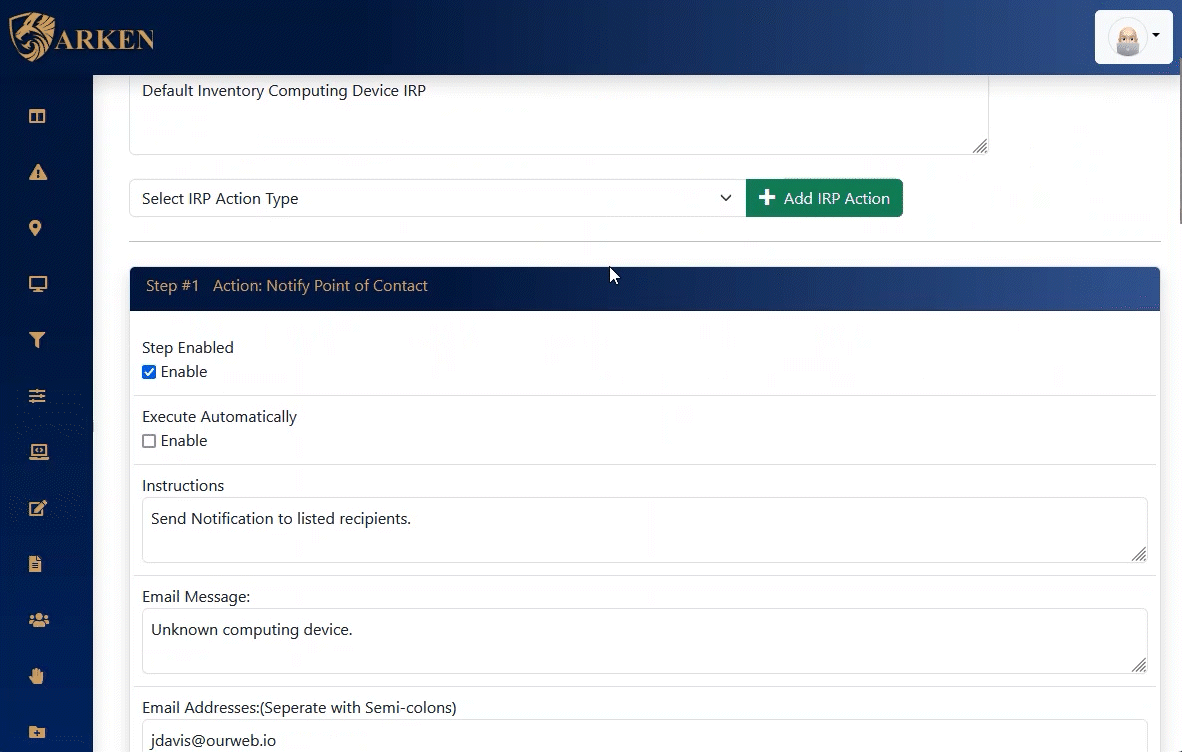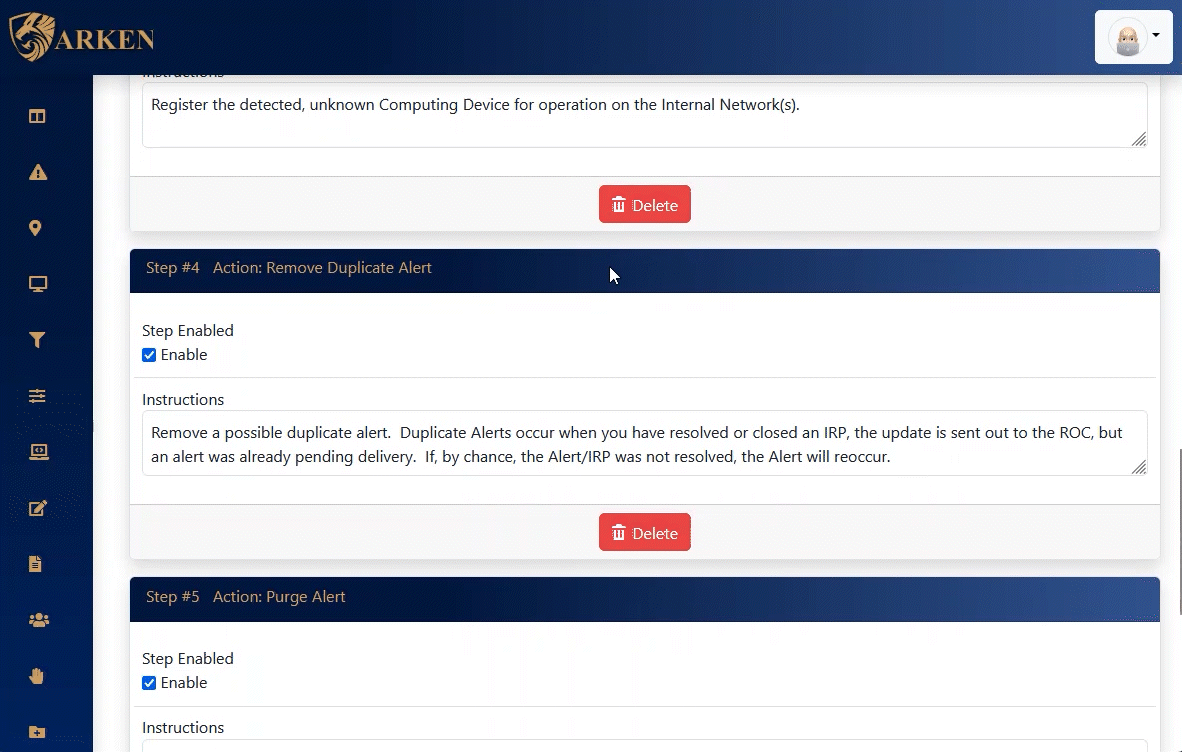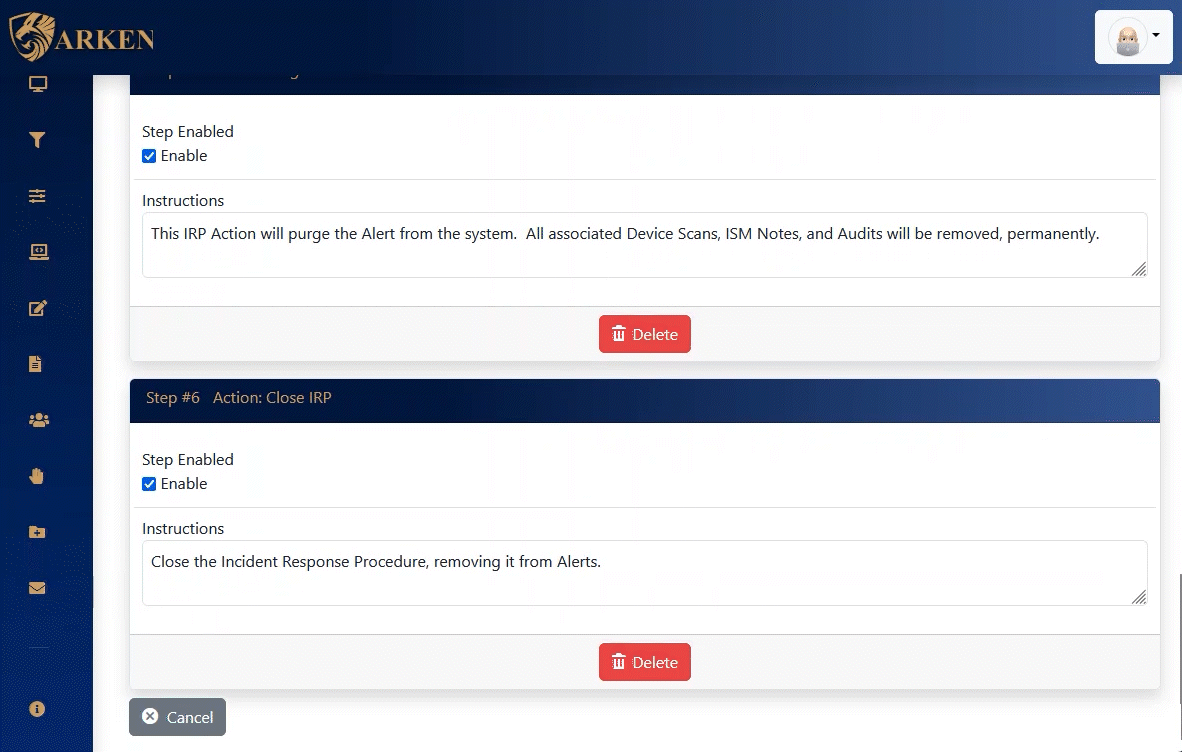
Incident Response Procedures – IRP
ARKEN supplies both automated and manual Incident Response Procedures. Using a checklist approach, Information Security events can be accurately mitigated in the shortest amount of time possible.
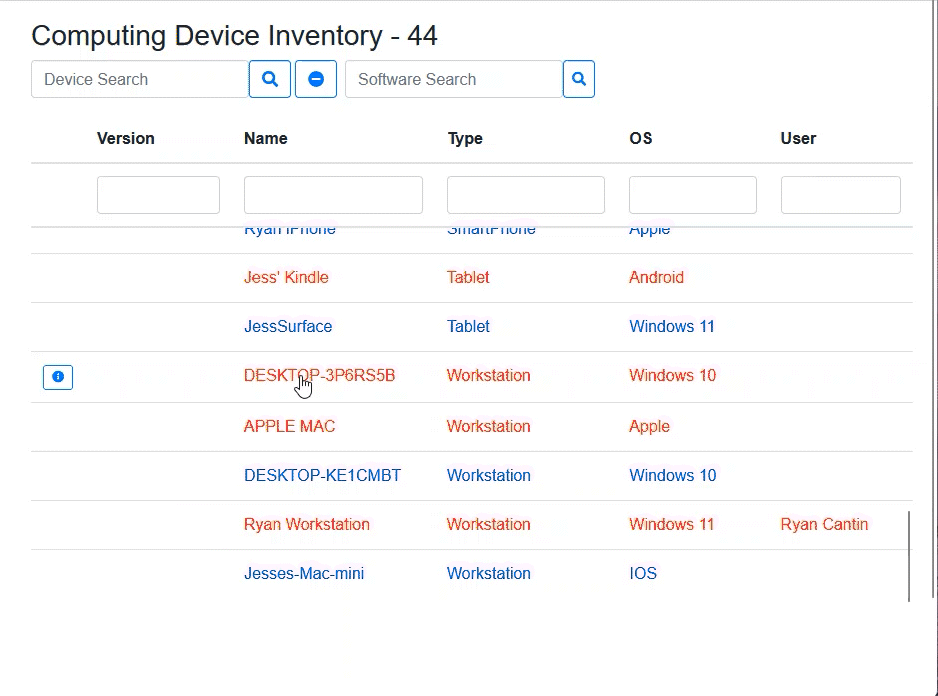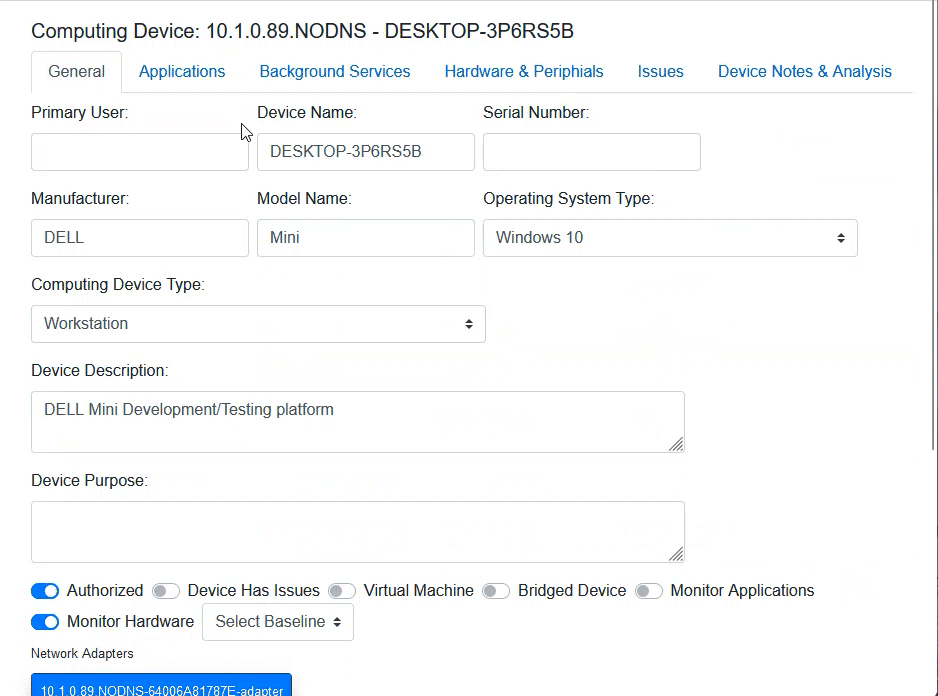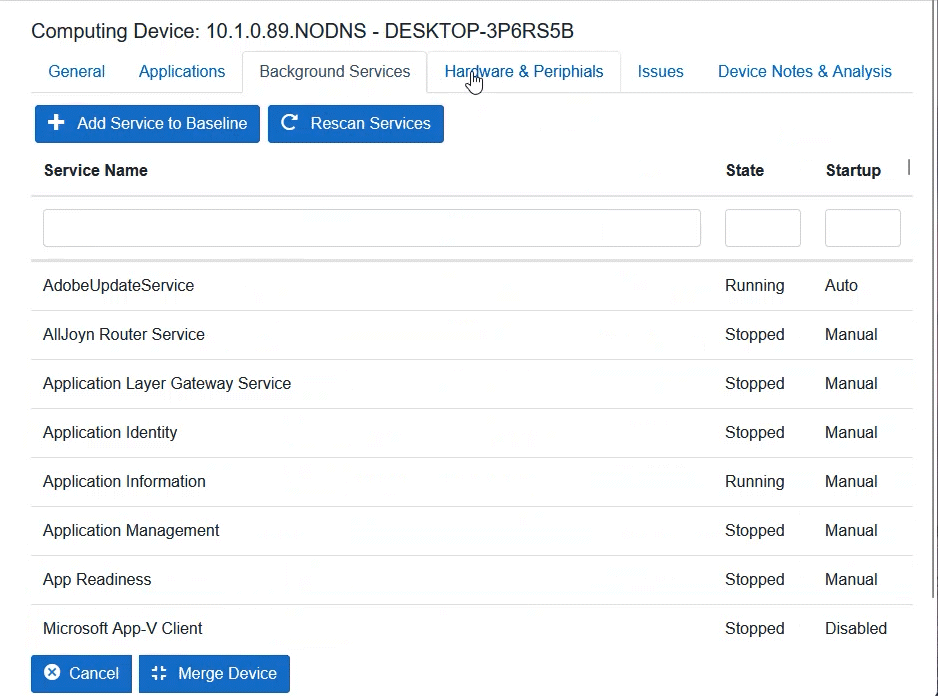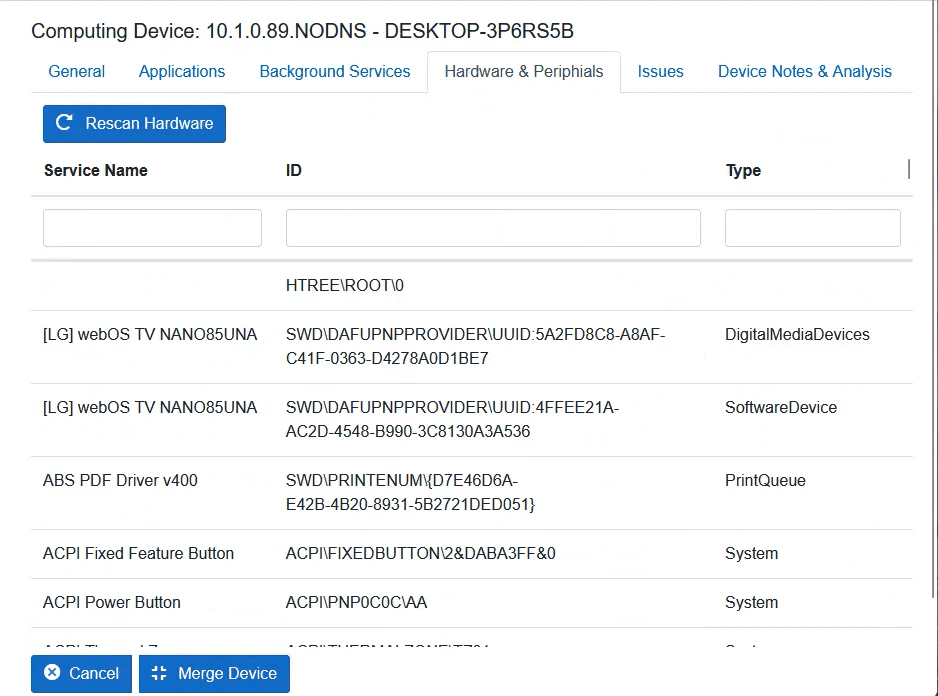
Computing Device Control
ARKEN provides control sensors for computing devices executing on Mac, Windows, or Linux operating systems. Implement software and hardware baselines to stop unwanted software installations. Prevent USB devices from being utilized or only those USB devices that have been authorized. Detect hardware and software changes and prevent unauthorized hardware/software from executing on the device.
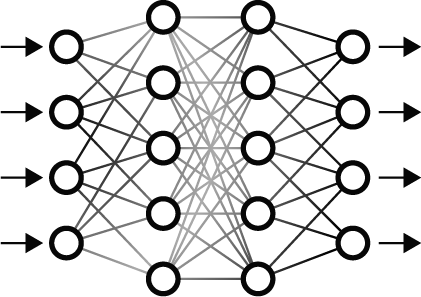
Behavioral Activity Monitoring
ARKEN employs several Neural Networks to track User and Network activity. The Neural Network classifies then determines if detrimental traffic is encountered, then invokes the correct Incident Response to mitigate and stop the behavior.

Policy
Information Security Policy contains the controls that ARKEN deploys. ARKEN implements a default NIST policy that can be modified to the specific organization’s culture. Further, the controls specified in the policy can be monitored and enforced; both manually and automatically.
When fully implemented, ARKEN can provide a real-time Information Security Posture report that will satisfy Information Security requests from Customers and 3rd party vendors. Thus, reducing the amount of effort required to fulfill these requests.
Reporting
ARKEN supplies a definitive list of reports for all aspects of operation, security reporting and analysis. From computing device inventory to alert activities, ARKEN’s reporting system allows a point-in-time snapshot of overall status and information security readiness.
Methodology
U.S. Air Force Colonel, John Boyd, created the concept of the OODA Loop to aid in the development of military strategy. By rapidly observing and analyzing an adversary’s behaviors, Col. Boyd believed that a strategist using the OODA decision-making process could gain an advantage. Currently utilized by NIST Cybersecurity Frameworks.
ARKEN has been built to implement this “advantage” to protect, defend, and proactively stop threats to Information Technology resources and the people who use it.
ARKEN implements Policy, Standards/Controls, and Procedures at each step of the OODA loop decision making process. This ensures that Information Security Compliance is met at all levels, and allows the generation of a real-time Security Posture.
Security Posture
ARKEN implements mapping and association of Policy sections/controls to its methodology. The OODA loop is mapped as follows:
- Observe – Policy
- Orient – Standards
- Decide – Controls
- Act
Once mapped, ARKEN generates a “real-time” security posture statement which will meet most requests for Information Security status and answer Information Security Questionnaires.
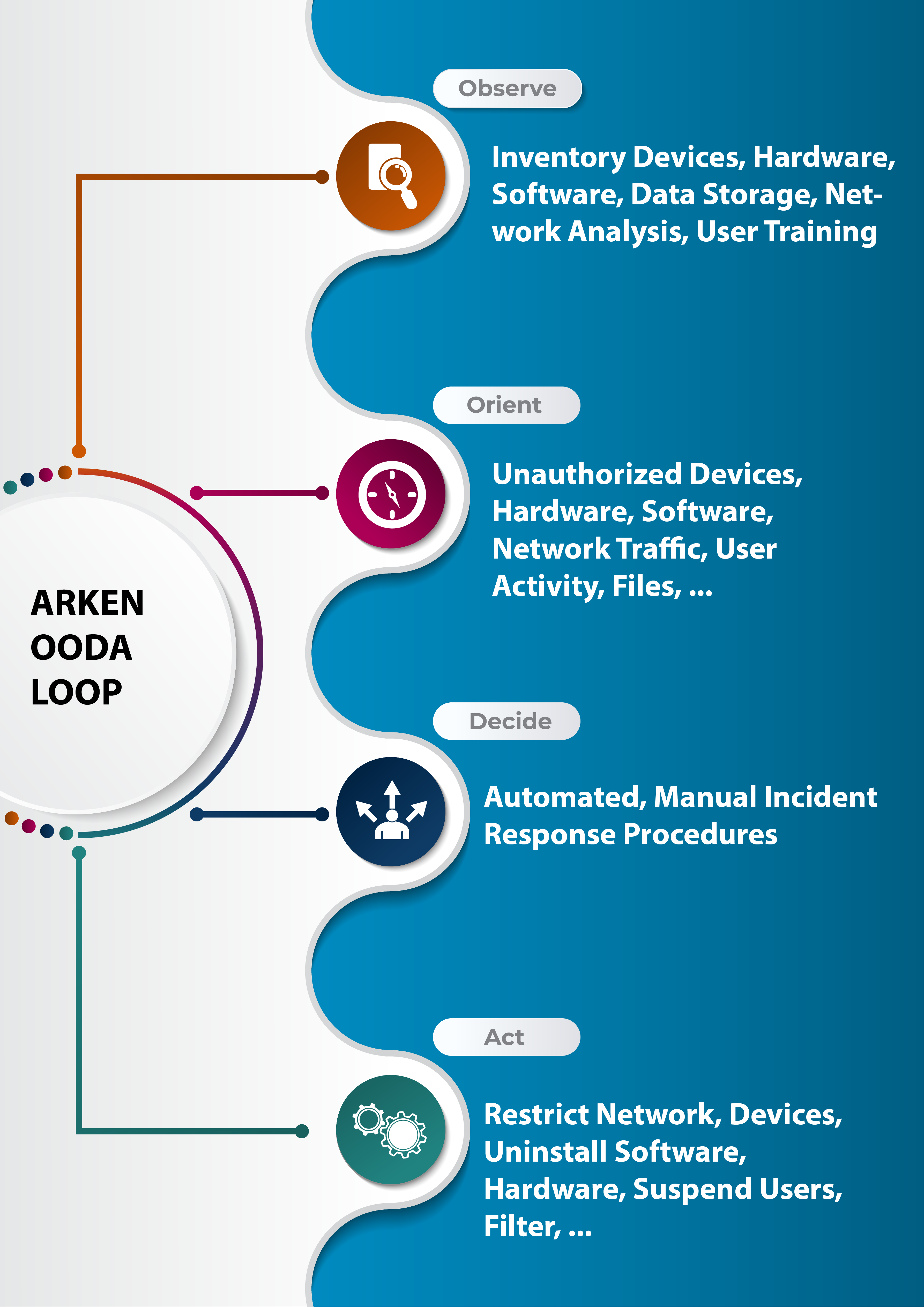
Observe
Most Information Security Engineers depend upon baselines. When working through a cybersecurity incident, these engineers place digital artifacts in “buckets”. These buckets categorize data which is then determined as “good” or “bad”. While a simple premise in theory, it is tedious and time consuming in reality.
ARKEN supplies the baseline organization. When established, any cybersecurity incident can be quickly, and more importantly, accurately diagnosed and mitigated. We take the complex and make it simple.
The following areas can be baselined by ARKEN:
ARKEN provides real-time tracking of Computing Devices that are in operation on a network. Computing Device detection is accomplished on multiple levels using scanning and network usage.
ARKEN contains the functionality to monitor and detect changes in Computing Device configurations. This includes Network Routers, Switches, and IoT devices.
ARKEN supplies the ability to inventory hardware and peripherals attached to a Computing Device and the software/applications which are installed on the device.
ARKEN scans and finds data stored on Computing Devices. This furnishes the ability to classify the data being stored or remove unnecessary storage.
Identify and track Users on Computing Devices on the network. ARKEN provides the capability to determine when and if a User should be accessing network attached resources.
Most organizations rely on edge detection and prevention, not realizing that the tools provided require a significant investment in time, talent, and treasure.
ARKEN reduces the time, talent, and treasure required to conduct accurate and ongoing network analysis.

Orient
ARKEN utilizes the information from the Observation step to localize cybersecurity incidents that occur within the network.
ARKEN uses the information from the (real-time) baselines to accurately define cybersecurity events. This orientation allows the incident to be quickly identified and for more accurate decision making.
ARKEN orientation includes:
- Alerts
- Unauthorized Computing Devices
- Hardware/Software changes
- Network Traffic anomalies
- Network Device configuration changes

Decide
At the core of ARKEN is the functionality to make accurate decisions, based on what is known about the environment.
These incident response procedures, IRPs, provides step-by-step instructions when combating a cybersecurity incident.

Act
ARKEN utilizes incident response procedures, IRPs, to act on cybersecurity incidents. These IRPs respond to raised alerts and enable automated or manual actions to be taken to mitigate the incident.
For example, whenever ARKEN detects unauthorized computing device peripheral hardware, the associated IRP automatically stops the hardware and then removes it from the computing device. Further, it can prevent unauthorized hardware from being re-attached, such as a USB Device.
All actions, automated or manual, are audited and tracked within ARKEN. ARKEN supplies detailed reporting on all activities.

