Cyber security done right!
Recon Secure Computing offers you the ability to both identify and control network traffic and software processes from the inside-out, as well as the outside-in!

One Platform, All Controls!
ARKEN is a hardware/software solution that bridges the gap between Information Security Controls and Information Technology Administration. Our platform gives you the ability to apply Information Security Policy, Standards, and Controls throughout the Information Technology Infrastructure and User base.
Get your data OUT of ‘The Cloud’ and secured from being taken by A.I. bots to feed someone else’s Large Language Model. Where traditional SIEM systems provide only coordination activities, ARKEN provides a complete security information event management system along with actionable event detections.
It’s YOUR data. YOU control it.
To steal ideas from someone is called plagiarism.
To steal from many is called research.
To steal from everyone is called A.I.
Internal Security Assessments
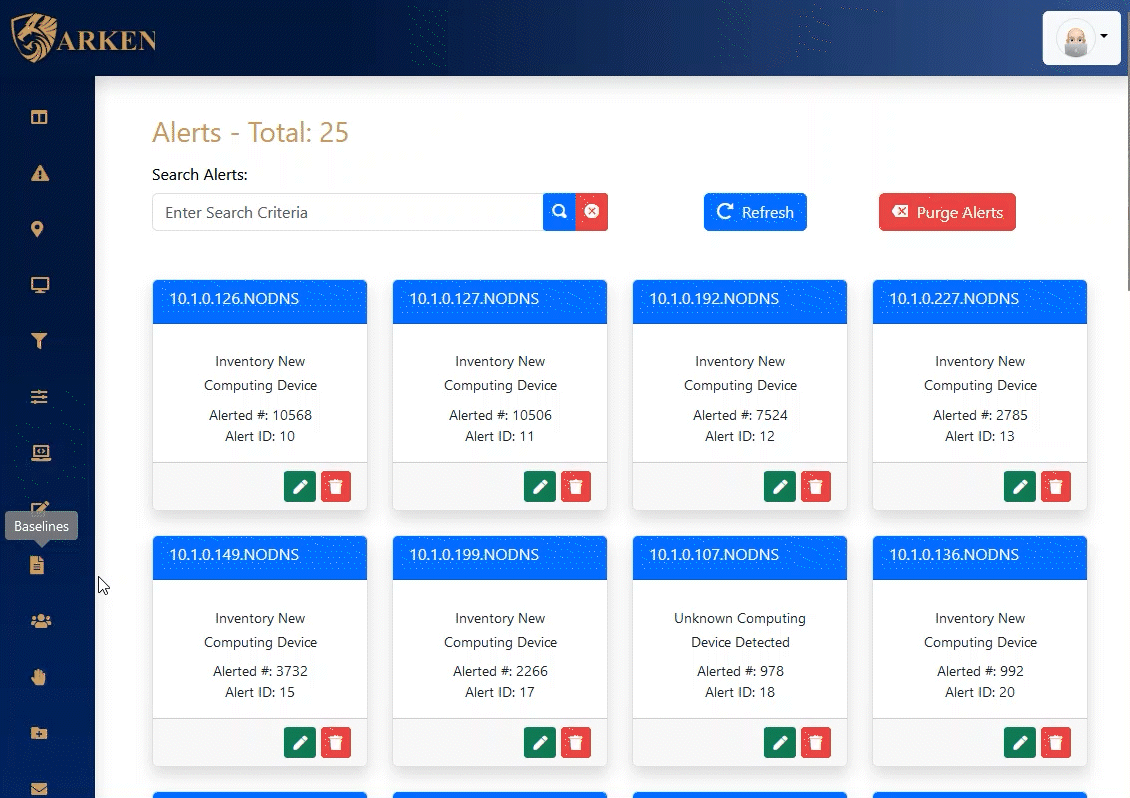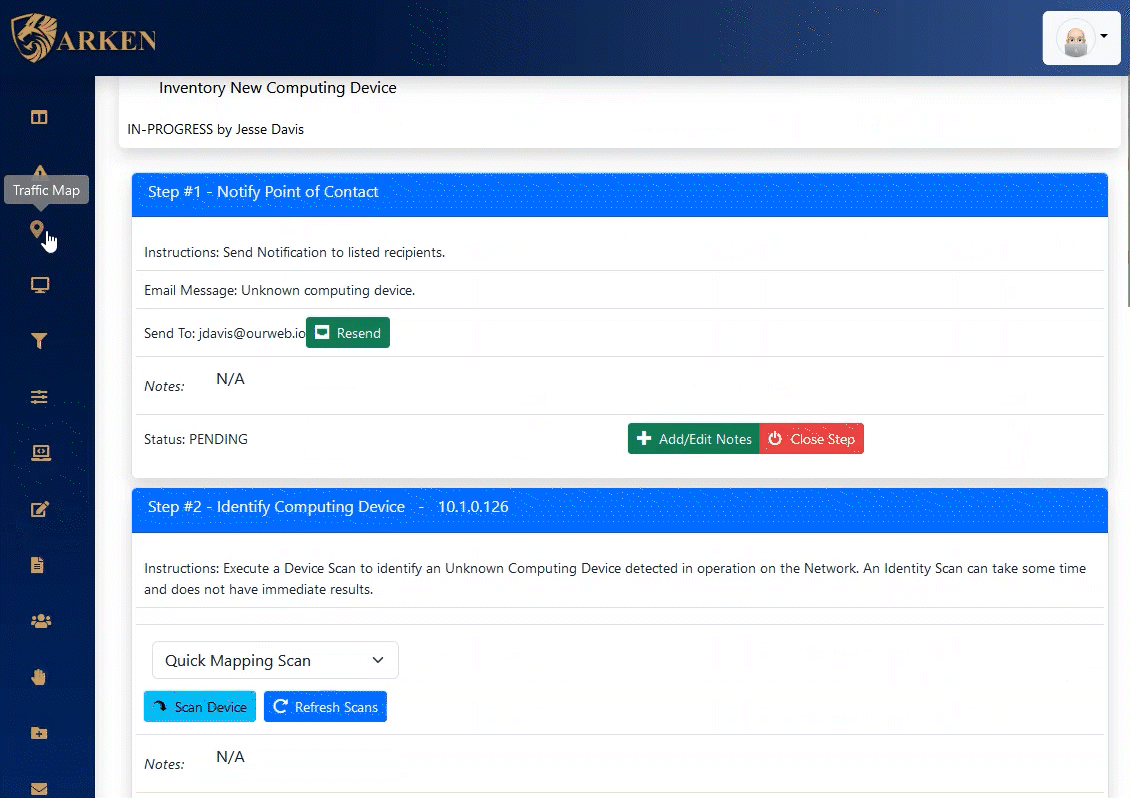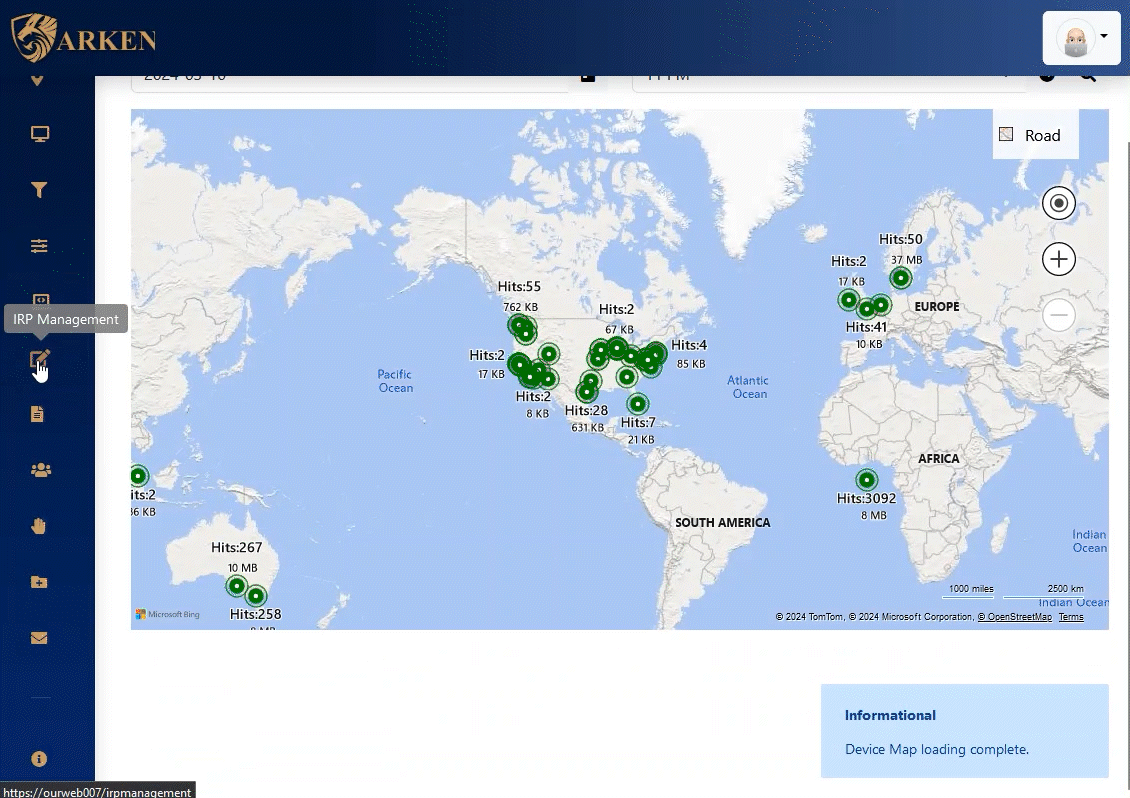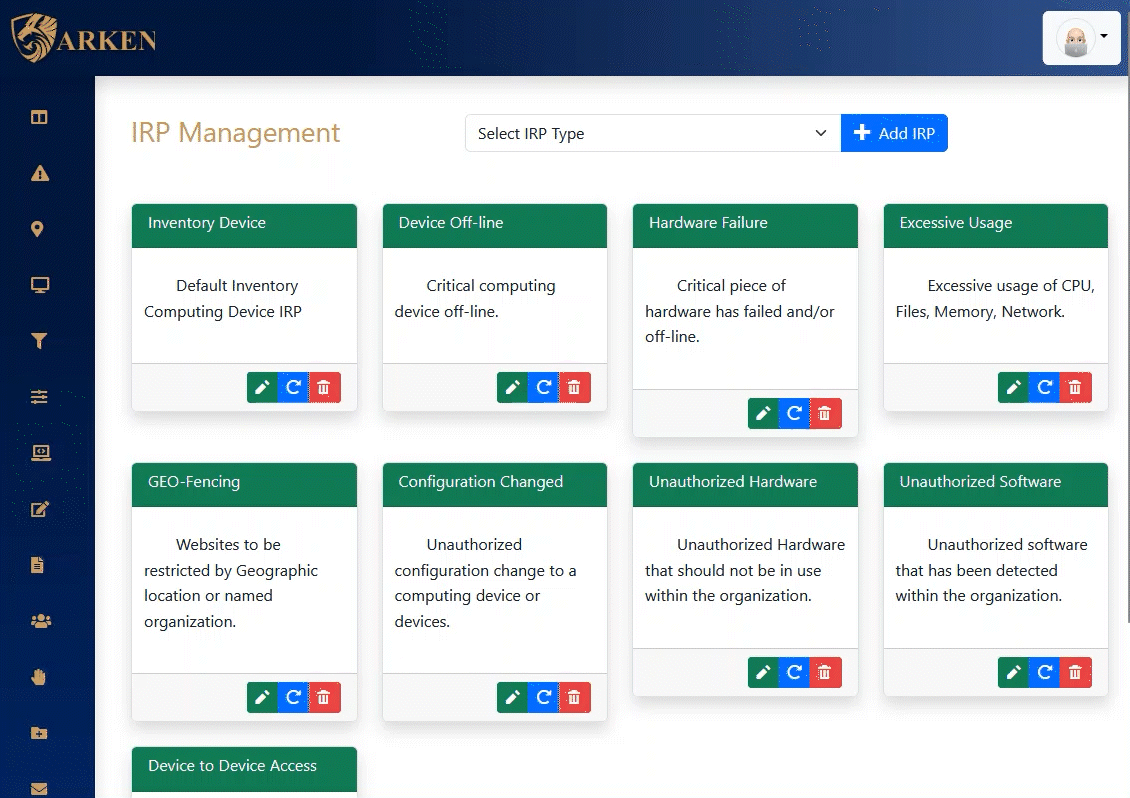
The Alerts dashboard in ARKEN provides a real-time, incident response-oriented approach to quick resolution of issues. Alerts are generated from defined Incident Response Procedures and can contain both automated and manual activities.
As alerts are worked, all aspects of the alert resolution are audited and reported.

External Security Assessments
Install ARKEN and it will discover all operational devices automatically. ARKEN furnishes identification scans and integrates with Active Directory and/or LDAP.

We also do business as OURweb, keeping families safe on the internet and protecting your right to free speech.


